- Download Genymotion .bin file
- Type command: chmod +x filename.bin
- ./filename.bin
- Create an account in Genymotion website.
- Log in to the the App.
- Click the "+" button on the top and add a device(phone model).
- Run this command in terminal:
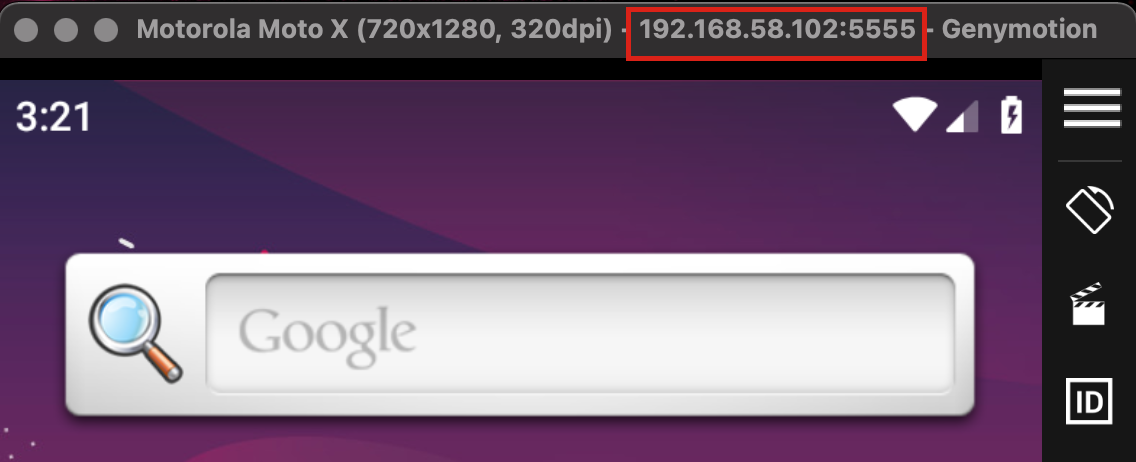
"docker run -it --rm \ -p 8000:8000 \ -p 1337:1337 \ -e MOBSF_ANALYZER_IDENTIFIER=<adb device identifier> \ opensecurity/mobile-security-framework-mobsf:latest" - In the <adb device identifier> add your value at his place
- docker run -it --rm \ -p 8000:8000 \ -p 1337:1337 \ -e MOBSF_ANALYZER_IDENTIFIER=192.168.58.102:5555 \ opensecurity/mobile-security-framework-mobsf:latest
- Press enter.
Start by defining a clear objective, such as exploiting a remote code execution (RCE) vulnerability or bypassing authentication on your target. Then, consider how you can achieve this goal using various attack vectors like XSS, SSRF, or others - these are simply tools to help you reach your objective. Use the target as how a normal user would, while browsing keep these questions in mind: 1)How does the app pass data? 2)How/where does the app talk about users? 3)Does the app have multi-tenancy or user levels? 4)Does the app have a unique threat model? 5)Has there been past security research & vulnerabilities? 6)How does the app handle XSS, CSRF, and code injection?


Comments
Post a Comment