Use the target as how a normal user would, while browsing keep these questions in mind:
1)How does the app pass data?
2)How/where does the app talk about users?
3)Does the app have multi-tenancy or user levels?
4)Does the app have a unique threat model?
5)Has there been past security research & vulnerabilities?
6)How does the app handle XSS, CSRF, and code injection?
crt.sh
crt.sh is used in bug bounty to discover subdomains of a target by searching for SSL/TLS certificates issued for the domain, which often reveal assets not listed publicly.
ffuf is a fast web fuzzer written in Go that allows typical directory discovery. Url path/parameter fuzzer.
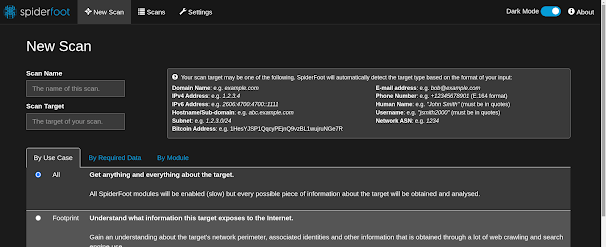
OSINT: spiderfoot
This package contains an open-source intelligence (OSINT) automation tool.
SpiderFoot can be used offensively, i.e. as part of a black-box penetration test to gather information about the target, or defensively to identify what information.
spiderfoot -l 127.0.0.1:5001This launches the web server interface accessible at http://127.0.0.1:5001In the web interface:
- Click on "New Scan".
- Enter the target (e.g., domain, IP, email, etc.).
- Configure the modules to enable specific types of information gathering (e.g., WHOIS lookups, subdomain discovery, or data breaches).
- Adjust scan options (e.g., depth, threading, API keys for external services).
Seclist (Password List)
SecLists is a comprehensive collection of penetration testing resources, including wordlists for usernames, passwords, URLs, APIs, fuzzing, and more, essential for security assessments.
This package contains an open-source intelligence (OSINT) automation tool.
spiderfoot -l 127.0.0.1:5001In the web interface:
- Click on "New Scan".
- Enter the target (e.g., domain, IP, email, etc.).
- Configure the modules to enable specific types of information gathering (e.g., WHOIS lookups, subdomain discovery, or data breaches).
- Adjust scan options (e.g., depth, threading, API keys for external services).
Nuclei templates
Nuclei is a fast, customizable, and open-source vulnerability scanner that uses YAML-based templates for detecting security issues.
haveibeenpwned
Brute force the login endpoints with common passwords found in haveibeenpwned’s Pwned Passwords API
bbr
An open-source tool to aid in command line-driven generation of bug bounty reports based on user-provided templates. Useful for piping reporting from one application to another (such as an automatic submission tool).
Video Tutorial:
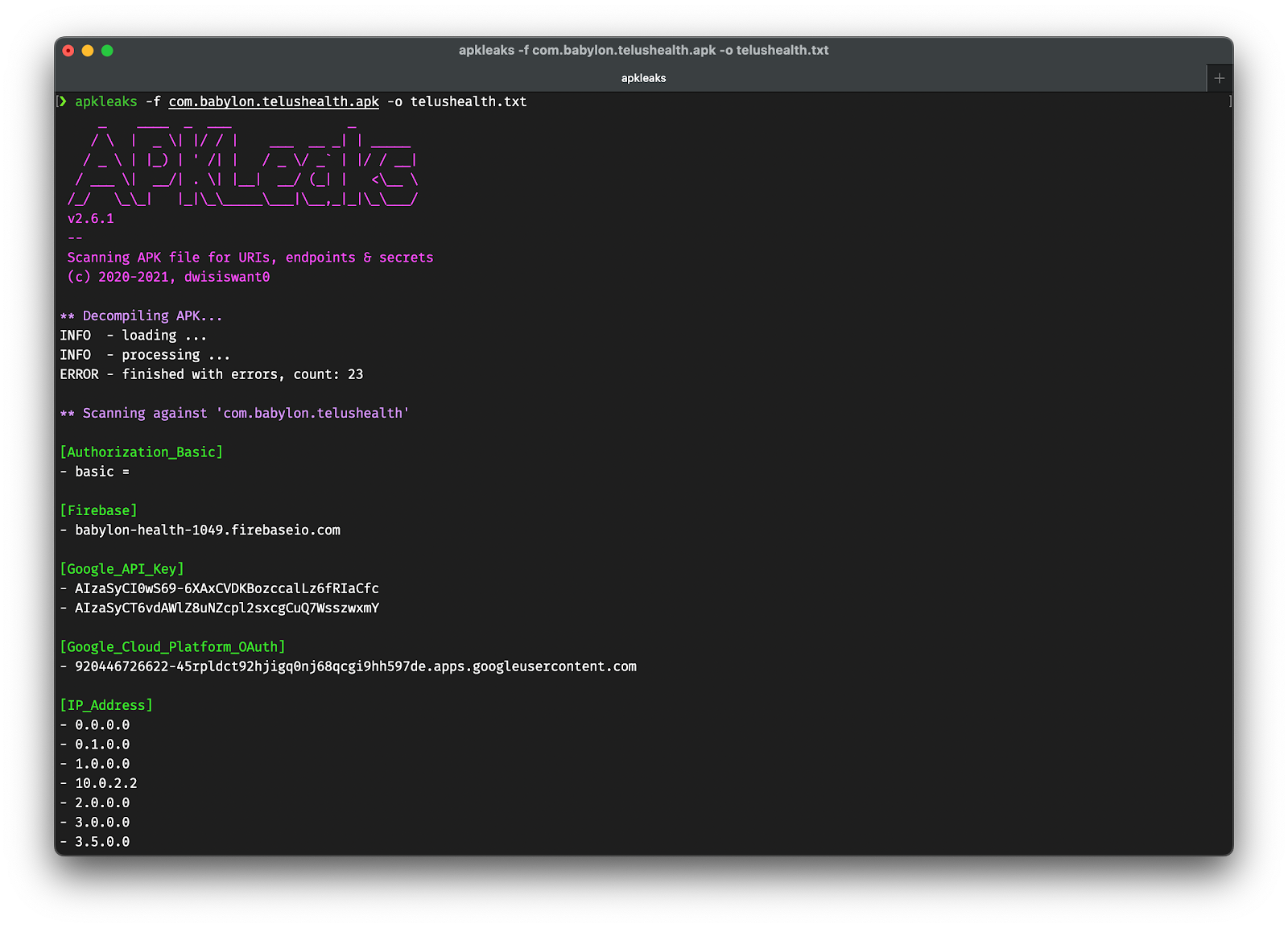
Scanning APK files for URIs, endpoints & secrets.
APKLeaks helps find sensitive data like API keys, passwords, private certificates, and other secrets embedded in Android APK files.
how to install
python3 apkleaks.py -f ~/Downloads/<app-to-test-android.apk >KeyHacks: validate API keys
nuclei token-spray
update or install nuclei
Test an API key against many API service endpoints
# Running token-spray templates against a single token to test nuclei -t token-spray/ -var token=random-token-to-test -esc # Running token-spray templates against a file containing multiple new line delimited tokens nuclei -t token-spray/ -var token=file_with_tokens.txt
If not working, Enable debugging to understand why no results are being returned:
nuclei -t /opt/token-spray/ -var token=tocken -esc -debug -vv
apktool
root@kali:~# apktool d <app_file.apk>
MobSF/Mobile-Security-Framework-MobSF
Mobile Security Framework (MobSF) is a security research platform for mobile applications in Android, iOS and Windows Mobile.
Quick setup with docker:
sudo docker pull opensecurity/mobile-security-framework-mobsf:latest
sudo docker run -it --rm -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latest
# Default username and password: mobsf/mobsf
#Dynamic Analysis
sudo docker run -it --rm \
-p 8000:8000 \
-p 1337:1337 \
-e MOBSF_ANALYZER_IDENTIFIER=127.0.0.1:6555 \
opensecurity/mobile-security-framework-mobsf:latest
Before running the command setup Genymotion here
sudo docker pull opensecurity/mobile-security-framework-mobsf:latest
sudo docker run -it --rm -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latest
# Default username and password: mobsf/mobsf
#Dynamic Analysis
sudo docker run -it --rm \
-p 8000:8000 \
-p 1337:1337 \
-e MOBSF_ANALYZER_IDENTIFIER=127.0.0.1:6555 \
opensecurity/mobile-security-framework-mobsf:latest
Before running the command setup Genymotion here
KiteRunner Api scanning
Kiterunner is a tool that is capable of not only performing traditional content discovery at lightning fast speeds, but also bruteforcing routes/endpoints in modern applications.
#vedio#
#list all wordlist
kr wordlist list# Run
kr scan <url> -A <name form wordlist>kr scan http://example.com -A raft-small-words
kr scan http://localhost -A apiroutes-240528
#save only the hashes and remove duplicates
cat output.txt | grep -oE '[a-zA-Z0-9]{20,}' > hashes.txt
sort hashes.txt | uniq > temp.txt && mv temp.txt hashes.txt
#vedio#
#list all wordlist
kr wordlist list# Run
kr scan <url> -A <name form wordlist>kr scan http://example.com -A raft-small-words
kr scan http://localhost -A apiroutes-240528
#save only the hashes and remove duplicates
cat output.txt | grep -oE '[a-zA-Z0-9]{20,}' > hashes.txt
sort hashes.txt | uniq > temp.txt && mv temp.txt hashes.txtGAU (GetAllUrls)
GAU (GetAllUrls) focuses primarily on historical URLs and subdomains in web applications. It comes pre-installed in Kali Linux.
waymore
Waymore is to find even more links from the Wayback Machine than other existing tools like gau.
Acunetix crack
Acunetix is an end-to-end web security scanner that offers a 360 view of an organization’s security.
Caido
Caido is a web application security tool like Burp Suite or OWASP ZAP.
Retire.js
Retire.js extension is a popular tool for scanning JavaScript libraries for known vulnerabilities.
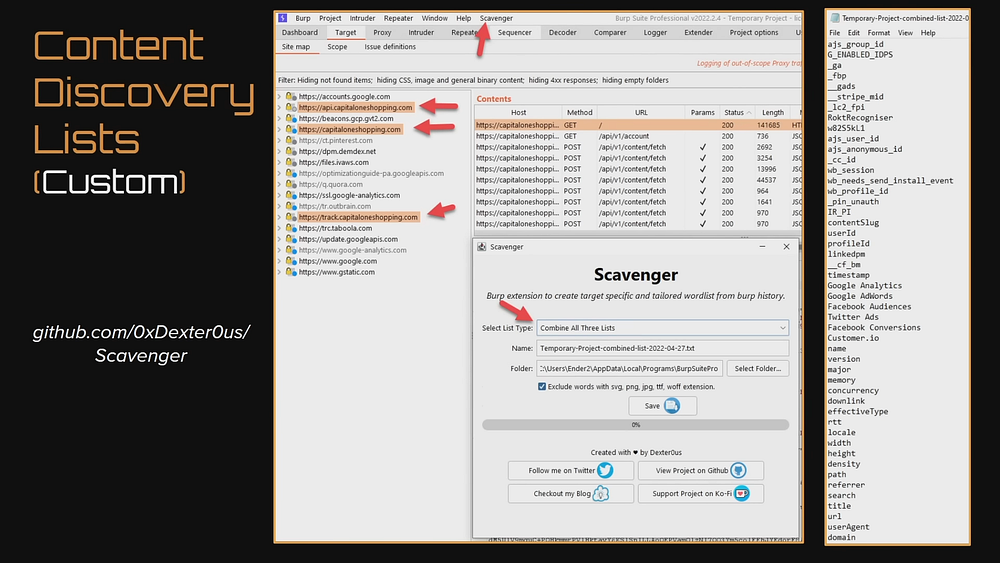
Scavenger
Burpsuite-Professional crack
Burp Suite Professional is a comprehensive, commercial tool widely used by security professionals, ethical hackers, and bug bounty hunters to test the security of web applications. It is developed by PortSwigger
chmod +x install.sh
./install.sh
chmod +x install.sh
./install.sh
change font
Kage
# Download source code git clone https://github.com/WayzDev/Kage.git # Install dependencies and run kage cd Kage yarn # or npm install yarn run dev # or npm run dev # to build project yarn run build
nip.io (Test SSRF) nip.io maps<anything>[.-]<IPAddress>.nip.ioin "dot", "dash" or "hexadecimal" notation to the corresponding<IP Address>:
- dot notation:
magic.127.0.0.1.nip.io- dash notation:
magic-127-0-0-1.nip.io- hexadecimal notation:
magic-7f000001.nip.ioSearch default credentialspip3 install defaultcreds-cheat-sheetcreds search tomcat
bbscope: Tool Github link
The quickest way to generate a scope to hack on. bbscope is a powerful scope aggregation tool for all major bug bounty platforms:
HackerOne
Bugcrowd
Intigriti
Immunefi
YesWeHack
For example, after installing the tool, you could run this command to fetch all BBP & VDP scope from Bugcrowd and save them in the bugcrowd-scope.txt.
bbscope bc -E "your_bugcrowd_email" -P "your_bugcrowd_password" -o u | tee bugcrowd-scope.txt
Portswigger Extensions
Request Minimizer:
This extension performs HTTP request minimization. It deletes parameters that are not relevant, such as random ad cookies and cache-busting nonces, etc..
Download the jython-standalone-2.7.4.jar file. Go to Settings > Extensions > Python environment & add the jar file.
Now, restart Burp Suite.
Now, install the minimizer extension.
TruffleHog Extension:

















Comments
Post a Comment