File and Binary Loading
r2 <binary>: Open a binary file.r2 -d <binary>: Open a binary in debugging mode.
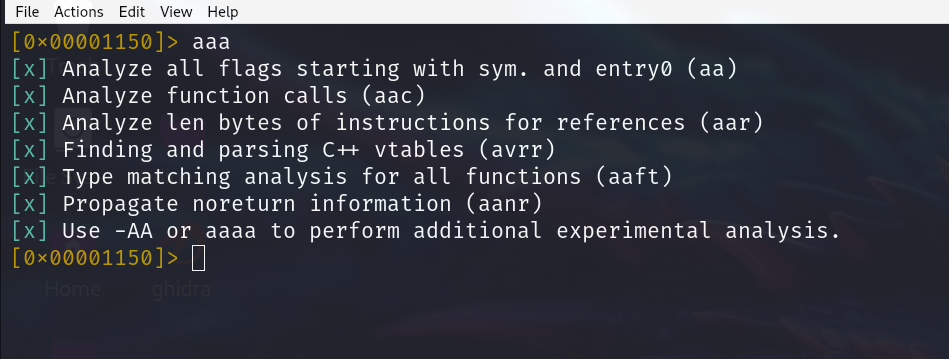
aaa
This is a shortcut for “analyze all." This command analyses our binary and looks for executable sections and looks for calls. when it finds a call, it looks for the destination of the call.
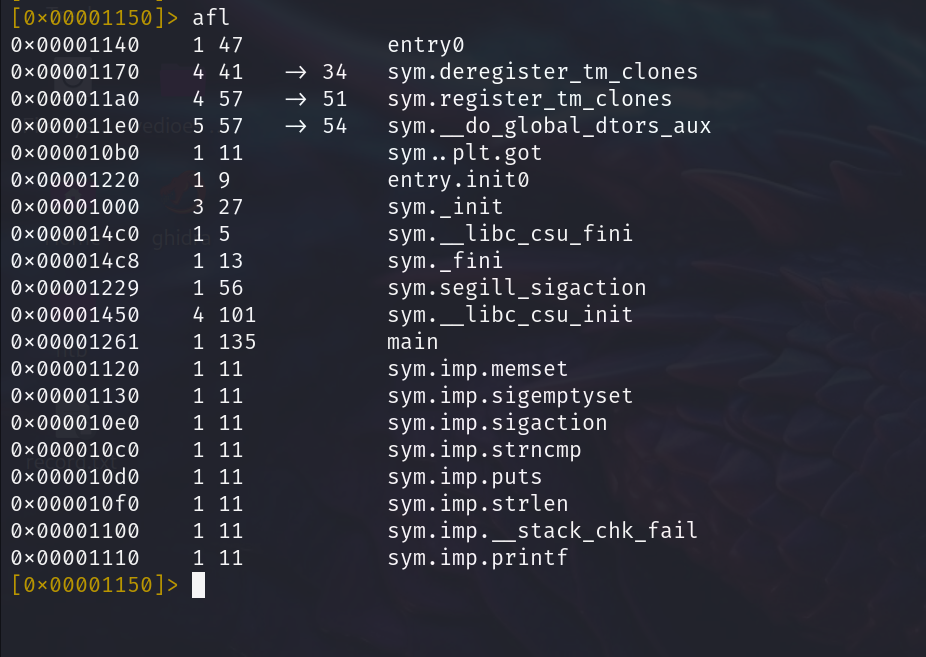
afl
Display all the functions in the code.
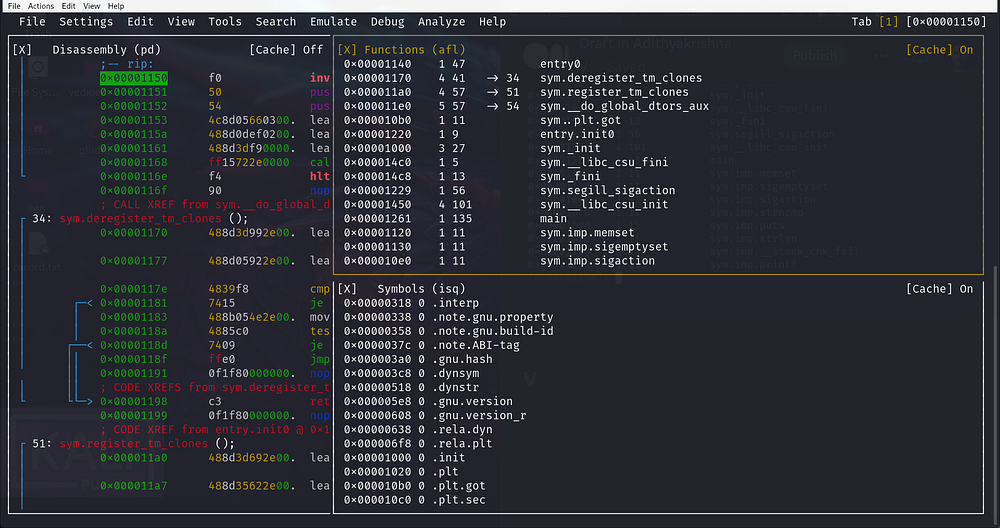
V
By pressing the capital letter V, show us all the different types of views the assembly view, graph views and the debugging view. Press the letter ‘p’ to navigate between the views.
pdf: Print the disassembled function where the current seek is.pdr: Print function recursively (entire call graph).af <address>: Analyze a specific function at<address>.
Navigation
s <address>: Seek to a specific address.s -ors +: Move backward or forward.s entry0: Seek to the program's entry point.s sym.main: Seek to themainfunction (if symbols are present)
Disassembly and Debugging
pd 10: Disassemble 10 instructions from the current address.px 32: Print 32 bytes in hex.db <address>: Set a breakpoint at<address>.dc: Continue execution.ds: Step into the next instruction.dso: Step over the next instruction.dr: Display or modify registers (e.g.,dr eax=0).
Searching
/c <string>: Search for a string./x <hex>: Search for a hexadecimal pattern./R <value>: Search for a specific value in memory.
Debugging in Visual Mode
V: Enter visual mode.F2: Set a breakpoint.F7: Step into.F8: Step over.F9: Continue execution
Information
i: General information about the binary.iI: Detailed imports information.ii: List of imports.is: List of symbols.ic: List of classes (if the binary uses C++ or similar).
Comments
Post a Comment