Reverse Engineering an API
If there is no documentation we will have to reverse-engineer the API based on our interactions. Mapping an API with several endpoints and a few methods can quickly become a large attack surface. To manage this process, build the requests under a collection to hack the API thoroughly. Postman can help you keep track of all of these requests.
Postman
Create a Workspace to save your collections. Use the Capture Requests button, found at the bottom right of the Postman window and select Enable proxy. Add your target URL to the “URL must contain” field, and click the Start Capture button.

Use FoxyProxy to route the traffic through Postman. Now browse the website as intended, go through all the functionalities like creating an account, adding a profile photo, changing email, uploading a video and so on.

Now go to the requests section of the postman and select all the API requests like the ones that are /api/, /v1/, etc.., then add to the collection. From the collection select a request and send it to see how the API provider is responding.
mitmweb
Use mitmweb to capture the requests and save the file(“flows”).

mitmproxy2swagger
mitmproxy2swagger is a tool that can be used to generate OpenAPI (formerly known as Swagger) specifications from HTTP traffic.
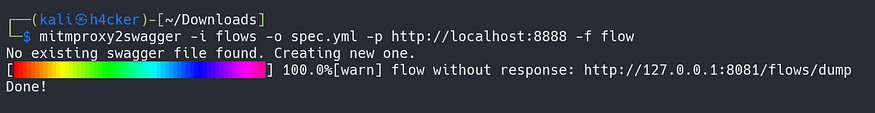
mitmproxy2swagger -i flows -o spec.yml -p <URL> -f flowvim spec.ymlNow remove the "ignore:" from the file where a /api is seen.Then run:mitmproxy2swagger -i flows -o spec.yml -p http://localhost:8888 -f flow --examples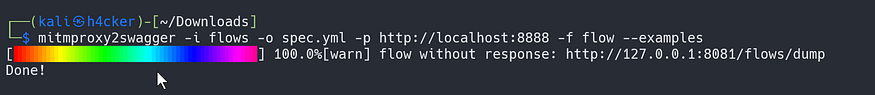
Now import the spec.yml file to postman:


Swagger editor
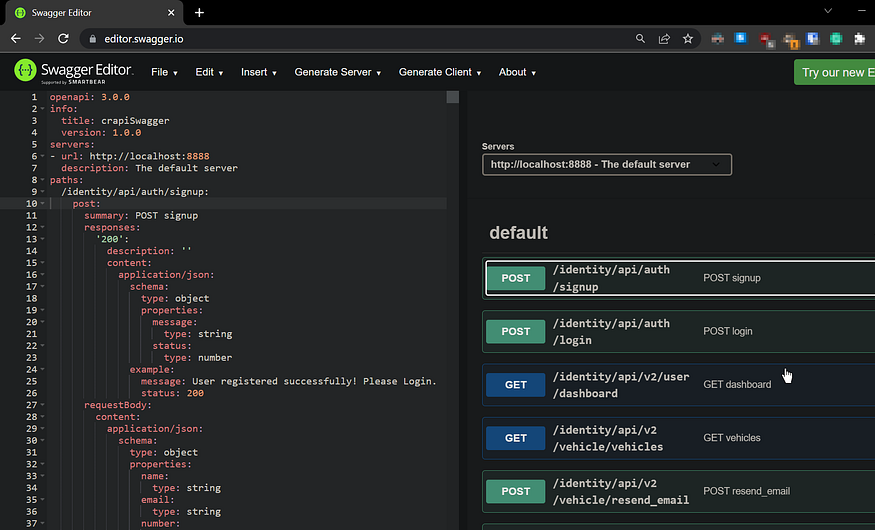
Import the spec.yml to the online swagger editor to get this view:
API Reconnaissance
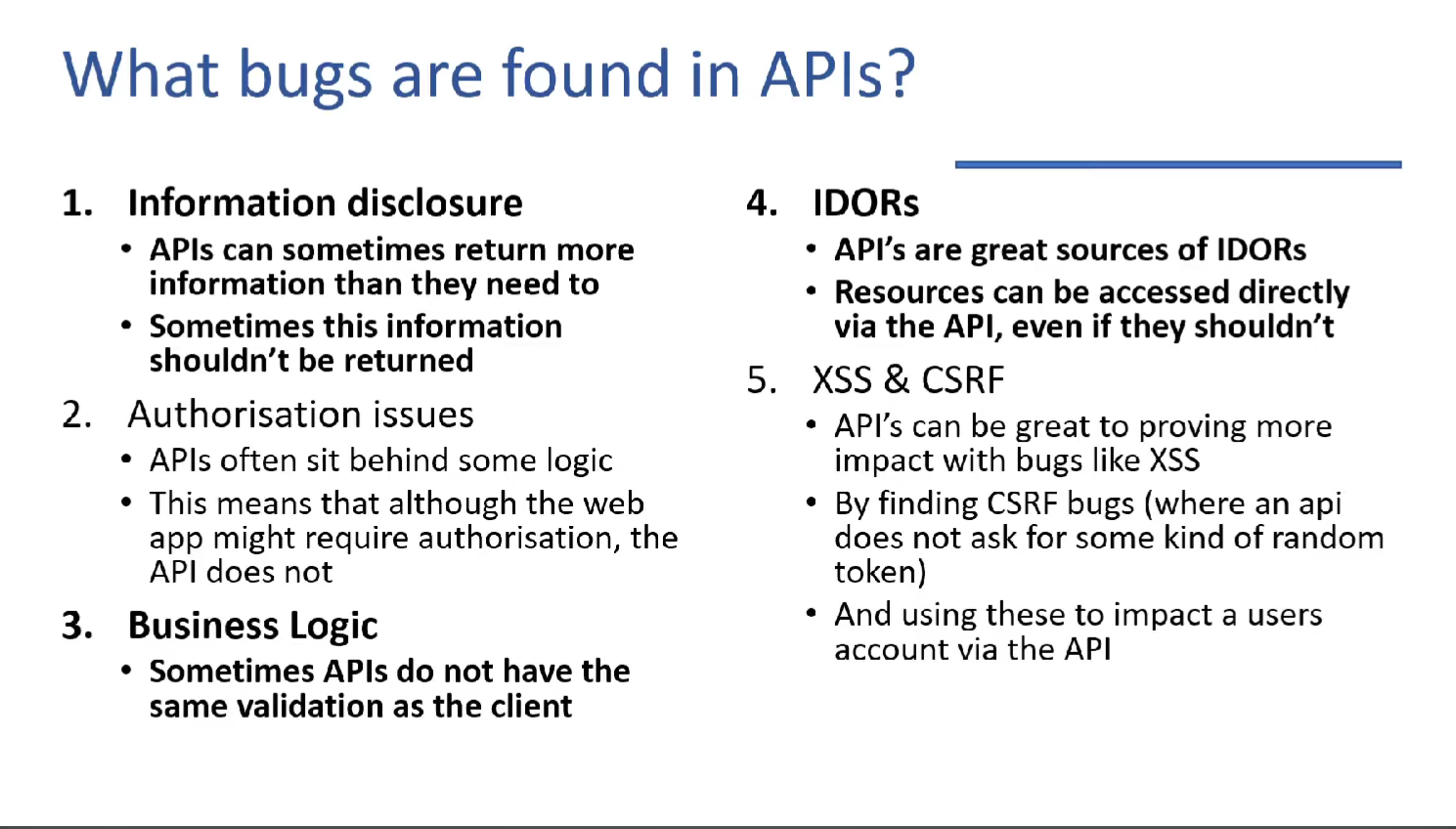
The goal here is to find APIs to attack and this can be accomplished by discovering the API itself or the API documentation.
Reconnaissance
Passive Reconnaissance
It is obtaining information about a target without directly interacting with the target’s systems.
Google Dorking
Firstly, google search for “<app name> API”.
intitle:” api” site:”google.com”
inurl:”/api/v2" site:”google.com”
inurl:”/api/v1" intext:”index of /”
inurl:json site:”google.com”
intitle:”index.of” intext:”api.txt”
intitle:”API Documentation” inurl:”/docs/”
ext:php inurl:”api.php?action=” | Finds all sites with a XenAPI SQL injection vulnerability. (This query was posted in 2016; four years later, there are currently 141,000 results.)
GitDorking

Search terms: Google api, exposed api key, shodan_api_key
extension:json NASA, filename:swagger.json
Search for common headers: “authorization: Bearer”
Always check the issues section and the commit section.
Use the tool Trufflehog, which is more efficient. Detailed video on how to use the Trufflehog GitHub tool and extension:
Shodan
hostname:”targetname.com”
“content-type: application/json”
http.title:”swagger” port:80,443
“graphql” port:80,443
“wp-json”
“content-type: application/xml”
CVEDB API — Fast Vulnerability Lookups: The CVEDB API offers a quick way to check information about vulnerabilities in a service.
InternetDB API: Fast IP Lookups for Open Ports and Vulnerabilities
Wayback Machine
The Wayback Machine is an archive of various web pages over time. This allows us to see changes to existing API documentation. Finding and comparing historical snapshots of API documentation can simplify testing for Improper Assets Management. If the API has not been managed well over time, there is a chance to find retired endpoints that still exist. These are known as Zombie APIs.

Active Reconnaissance
Get recruted at nso:amass
Command-line tool to find target subdomains by collecting OSINT from over 55 different sources.
amass enum -active -d target-name.com |grep api
amass enum -passive -d target-name.com |grep api
In active mode, Amass actively interacts with the target’s infrastructure, such as by sending DNS queries or performing port scans. This approach might reveal more information but also runs the risk of being detected by the target’s security systems (e.g., intrusion detection systems, firewalls).
In passive mode, Amass does not directly interact with the target’s infrastructure. Instead, it gathers information from third-party sources such as public databases, search engines, and DNS records. This method is stealthier and less likely to be detected by the target.
Devtools
Open devtools and right-click the file section to add URL.

Now browse through the application and check for api calls. To interact with the request right-click the request and copy it as cURL, then use Postman to import >raw text > paste the curl request, then interact with it.
Kiterunner
Assetnote page on kiterunner.
Kiterunner is currently the best tool available for discovering API endpoints and resources.
git clone https://github.com/assetnote/kiterunner.git
# build the binary
make build
# symlink your binary
ln -s $(pwd)/dist/kr /usr/local/bin/krkr wordlist list
Comments
Post a Comment